Overview
VPN: Azure to on premise
Overview
Microsoft Azure provides a site to site VPN gateway service for when you need to connect Azure services to on site services without them being public facing. Traffic is encrypted between an Azure virtual network and an on-premises location over the public Internet.
Acronyms used in this document:
- AVD - Azure Virtual Desktop (Microsoft's platform for delivering Windows shared/personal virtual desktops/applications via Azure)
- RDS - Remote Desktop Services (Microsoft's suite of services for delivering thin clients with a full desktop or 'remote apps' via the Windows server operating system)
- AD - Active Directory (An instance of an Microsoft Active Directory Domain Services install on a physical server, VM in azure, etc)
- VM - Azure Virtual Machine
- DNS - Domain Name System is a hierarchical and decentralized naming system for computers, services, or other resources connected to the Internet or a private network. Most prominently, it translates more readily memorized domain names to the numerical IP addresses needed for locating and identifying services and devices with the underlying network protocols.
- VNET - An Azure Virtual Network found here: https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FvirtualNetworks
Common reasons for a On-Premise to Azure VPN:
- AD replication between an on premise AD domain controller (DC) and a Azure VM DC
- Replication of services between on premise and Azure such as Scale Out File Server or Exchange Mail Server
- To enable specific peripheral access such as on site printers or scanners
- To allow access to services such as RDS or intranet without making them public facing
- Temporary VPN for data transfer, migration or testing to Azure
Requirements:
- An Azure tenant and subscription
- Your Azure VNET address should usually be separate from your on site private address space:
- Example. Azure VNET is usually 10.10.0.0/16, where as onsite may be 10.0.0.0/24.
- A VPN device that supports:
- Internet Protocol Security (IPsec) suite based VPN's
- Internet Key Exchange (IKEv1 or IKEv2) protocol
- IKE Authentication Method: Pre-Shared Key
- One of the following encryption / hashing Algorithms:
- 1. AES256 / SHA1
2. AES256 / SHA256
3. AES128 / SHA1
4. AES128 / SHA256
5. 3DES / SHA1
6. 3DES / SHA256
- 1. AES256 / SHA1
- For detailed requirements for your VPN device see: https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devices
Part 1 - Create an Azure Gateway Subnet
- In most cases you will already have an Azure Virtual Network. Select your network under: https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FvirtualNetworks
- Select Subnets
- Click "+Gateway Subnet" and select appropriate options (usually default is correct)
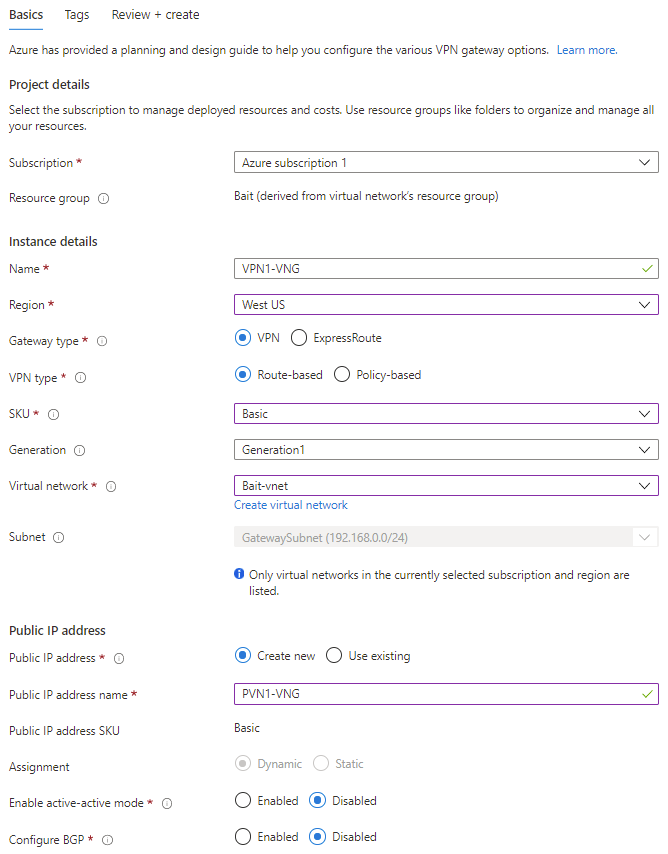
Part 2 - Create an Azure Virtual Network Gateway
- Navigate to: https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FvirtualNetworkGateways
- Click "+Create"
- Select appropriate values then "Review + create"
- Most customers select VPN + Route Based for type
- See here for information on SKU: https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-gateway-settings#gwsku
- For further information see: https://docs.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portal#create-the-gateway
- Screen shot example settings:
- Click "Create"
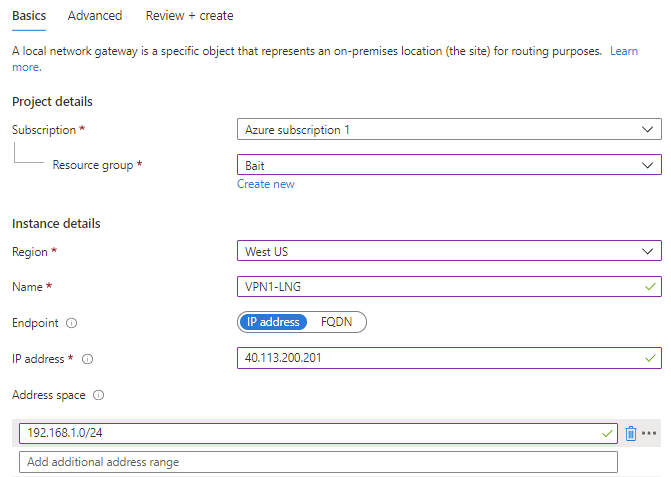
Part 3 - Create an Azure Local Network Gateway
- Navigate to: https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2Flocalnetworkgateways
- Click "+Create"
- Select appropriate values then "Review + create"
- IP address is usually the public IPv4 address of your on site VPN device
- Address space is usually your on site private IPv4 address space
- For further information see: https://docs.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portal#LocalNetworkGateway
- Screen shot example settings:
- Click "Create"
Part 4 - Configure your on-site VPN device
This procedure will be different depending on the vendor of your on site device. This part will require specific knowledge of your on site device.
- For further information see: https://docs.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portal#VPNDevice
- Validated VPN devices: https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devices#devicetable
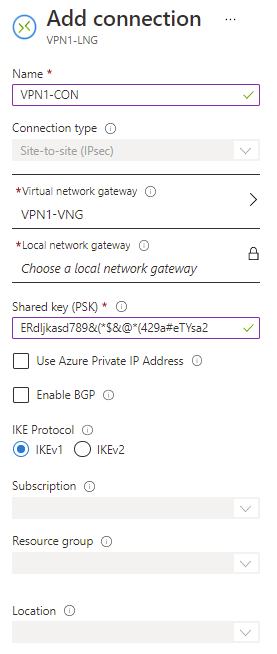
Part 5 - Connect the VPN
- Navigate to: https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2Flocalnetworkgateways
- Select the Gateway you created in Part 3.
- Click "Connections"
- Click "+Add"
- Select appropriate values:
- The PSK will have been created when you setup your on site VPN device
- Further information: https://docs.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portal#CreateConnection
- Screen shot example settings:
- Click "Ok"
- You should see Connected under status in connections once the VPN is active.
Part 6 - Test the VPN
There are various ways to test the VPN which are outside of the scope of this document however some examples are:
- Ping an IP address from an Azure VM to an on site device. Make sure ICPM/Ping is allowed through any routers/firewalls/switches/operating-systems that the request will travel via.
- Access a service such as a Windows share ( Example \\10.0.0.10\share ) from one side of the VPN to the other. Make sure this service is allowed through any routers/firewalls/switches/operating-systems that the request will travel via.
- Test DNS resolution. Similar as above but try "ping myhost.mydomain.local" or \\myhost\share
Appendix
DNS Considerations
There are many ways to configure DNS in an on-site to Azure VPN based hybrid environment. In most MCIT RDS or AVD environments we suggest to keep the existing Azure DNS settings as they were configured by our wizard. In a simple environment to allow DNS resolution from RDS or AVD machines to on internal on-site devices add relevant DNS entries or a new zone to the DNS server running on MSDC-001.
The second scenario is when you have an on site DC and an Azure DC that are part of the same forest, in this case the AD integrated DNS zones will be updated to each other. The Azure DC will resolve DNS for Azure VM's and the on-site DC will resolve DNS for the on-site devices.